7 centos7下Firewall使用详解 [进阶篇]
1 | https://www.cnblogs.com/yang-dan/p/12090773.html |
1. firewalld放行端口
8081/tcp,8082/tcp,8083/tcp [用一行代码]
1 | firewall-cmd --zone=public --permanent --add-port={8081/tcp,8082/tcp,8083/tcp} |
2. firewalld放行服务
http,https [用一行代码]
1 | firewall-cmd --zone=public --permanent --add-service={http,https} |
3. 自定义服务名称—>服务对应的端口 8081 8082 8083 –>api业务
1 2 3 | cd /usr/lib/firewalld/services/ cp http.xml api.xml vi api.xml |
1 2 3 4 5 6 7 | <?xml version="1.0" encoding="utf-8"?> <service> <short>API (HTTP)</short> <port protocol="tcp" port="8081"/> <port protocol="tcp" port="8082"/> <port protocol="tcp" port="8083"/> </service> |
1 2 | firewall-cmd --reload firewall-cmd --zone=public --permanent --add-service=api |
4. 转发-相同IP,转发到不同端口
端口4443 转发到 端口22
source address=”192.168.122.1/24″
端口 4443 —-> 端口22
1 2 3 | firewall-cmd --permanent --add-masquerade firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.122.1/24" forward-port port="4443" protocol="tcp" to-port="22"' firewall-cmd --reload |
连接192.168.122.52的4443端口
1 | ssh root@192.168.122.52 -p 4443 |
5. 转发- 转发到不同IP,不同端口
source address=”192.168.122.1/24″
任何人访问192.168.122.112 5555端口都给转发
192.168.122.1 —> 192.168.122.112 5555 —> 192.168.122.21 22
1 2 3 | firewall-cmd --permanent --add-masquerade firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.122.1/24" forward-port port="5555" protocol="tcp" to-port="22" to-addr="192.168.122.21"' firewall-cmd --reload |
连接192.168.122.112 5555端口
1 | ssh root@192.168.122.112 -p 5555 |
6. 允许192.168.122.1主机能够访问 http服务
source address=”192.168.122.1/24″
1 | firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.122.1/24" service name="http" accept' |
7. 允许192.168.122.1/24能访问API服务
source address=”192.168.122.1/24″
1 | firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.122.1/24" service name="api" accept' |
8. 默认public区域对外开放所有人能通过ssh服务连接,*但拒绝192.168.123.1/24网段通过ssh连接服务器
source address=”192.168.123.1/24″
1 | firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.123.1/24" service name="ssh" drop' |
9. 只有192.168.122.1/24主机可以访问ssh服务*[使用2222端口]
source address=”192.168.122.1/24″
2222端口
1 | firewall-cmd --zone=public --permanent --add-rich-rule='rule family="ipv4" source address="192.168.122.1/24" port port="2222" protocol="tcp" accept' |
10. firewalld实现共享上网
在指定的带有公网IP的实例上启动Firewalld防火墙的NAT地址转换,以此达到内部主机上网。
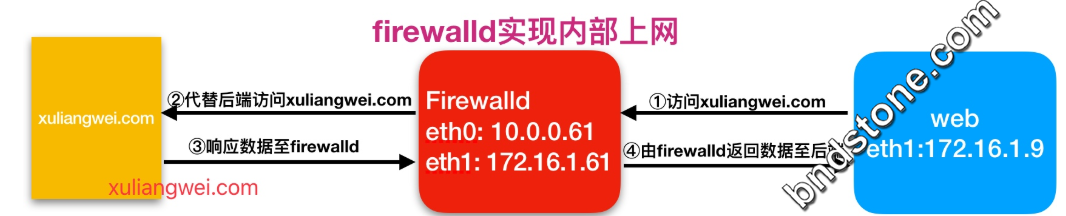
详细流程
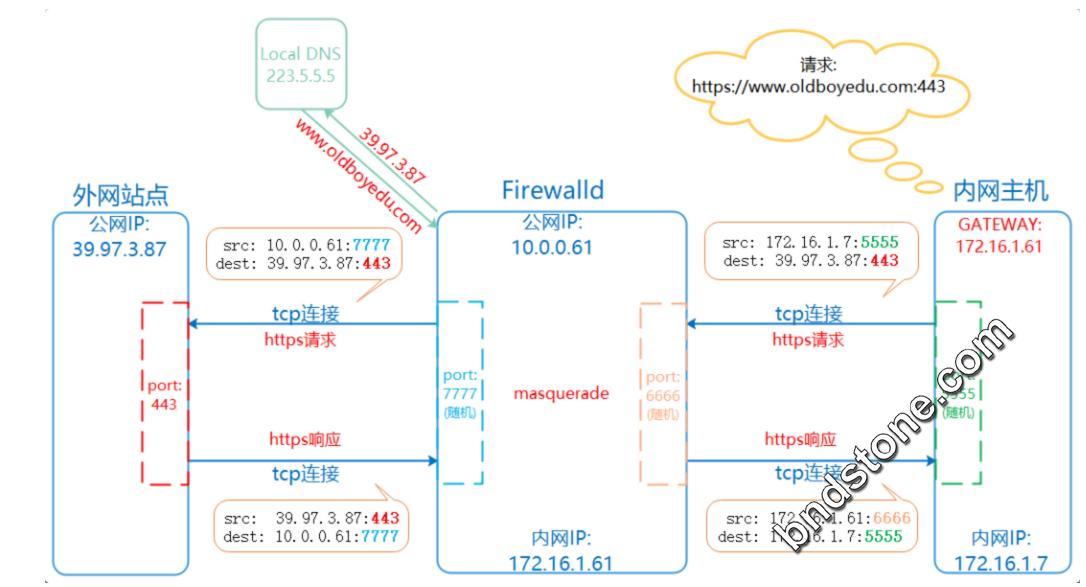
10-1: firewalld防火墙开启masquerade, 实现地址转换
1 2 | firewall-cmd --permanent --add-masquerade firewall-cmd --reload |
10-2: 客户端将网关(eth1)指向firewalld服务器,将所有网络请求交给firewalld
1 | vi /etc/sysconfig/network-scripts/ifcfg-eth1 |
1 | GATEWAY=172.16.1.61 |
10-3: 客户端还需配置dns服务器
1 | vi /etc/resolv.conf |
1 | nameserver 223.5.5.5 |
10-4: 重启网络(eth1),使其配置生效
1 | ifdown eth1 && ifup eth1 |
10-5: 测试后端web的网络是否正常
1 | ping www.baidu.com |