23 CentOS 7 使用Google-Authenticator进行多因素认证
1 | http://blog.51cto.com/41084/1952500 |
1. 安装所需的软件:
1 2 | yum update -y yum install -y autoconf automake libtool pam-devel git qrencode |
2. 安装google-authenticator
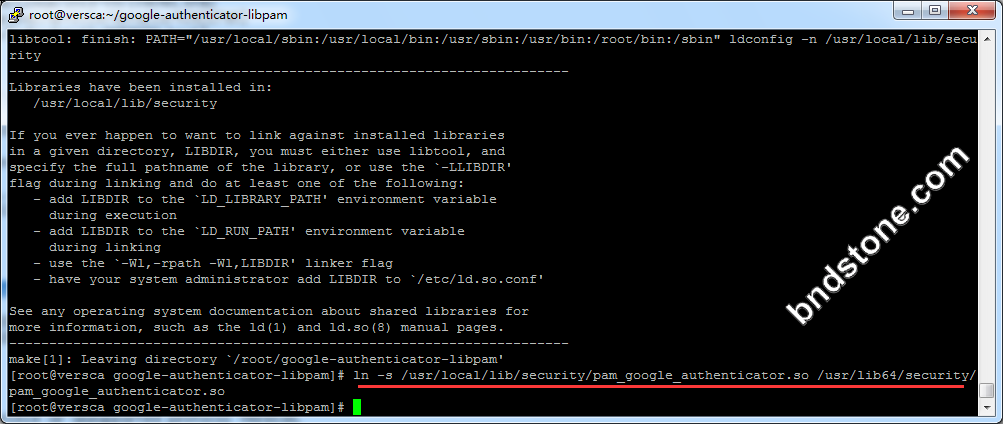
1 2 3 4 5 6 7 | git clone https://github.com/google/google-authenticator-libpam.git 或 git clone https://gitee.com/ancky2006/google-authenticator-libpam.git cd google-authenticator-libpam/ ./bootstrap.sh ./configure make make install ln -s /usr/local/lib/security/pam_google_authenticator.so /usr/lib64/security/pam_google_authenticator.so |

3. 配置openssh,
1 | vi /etc/pam.d/sshd |
1 | auth required pam_google_authenticator.so nullok #加在最上面一行 |
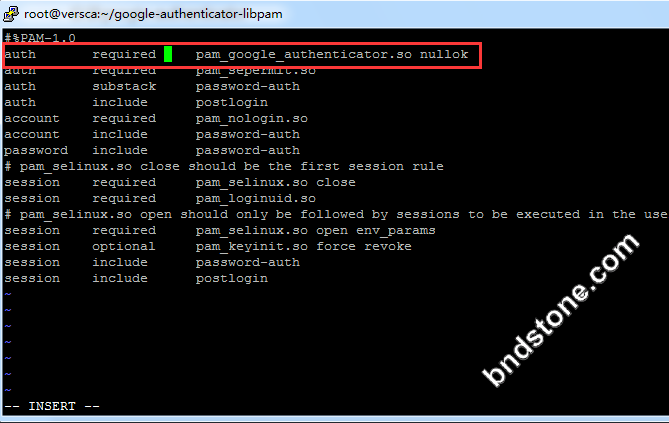
编辑/etc/ssh/sshd_config为
1 | vi /etc/ssh/sshd_config |
1 | ChallengeResponseAuthentication yes //这边no要改成yes |
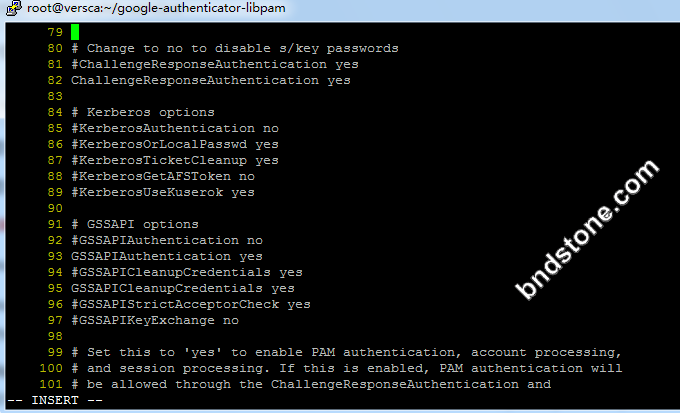
4. 重启sshd
1 | systemctl restart sshd.service |
5. 为用户启用google-authenticator
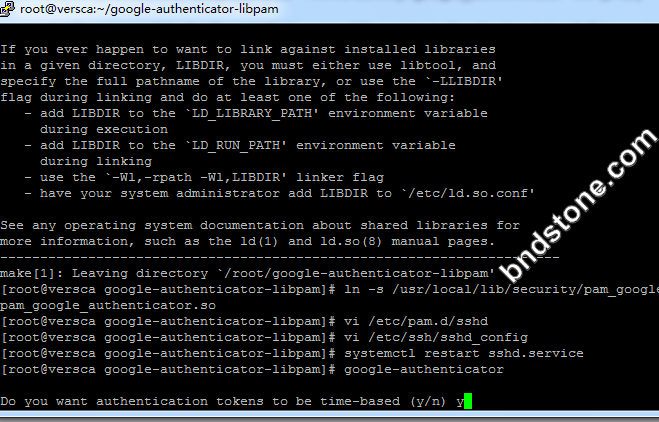
1 | google-authenticator |
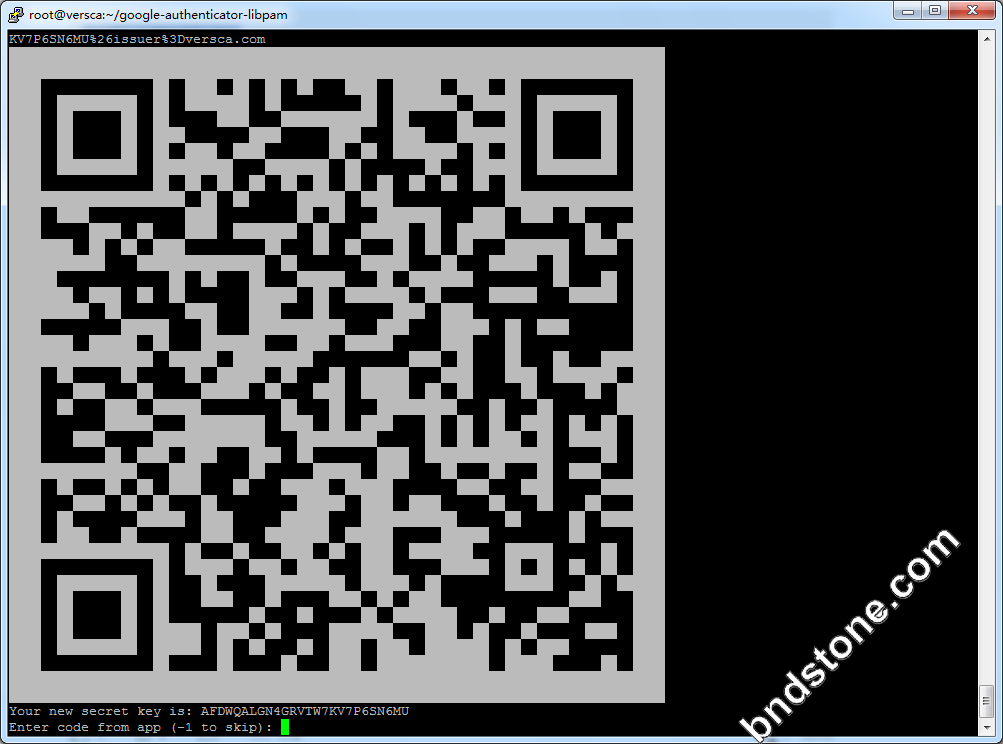
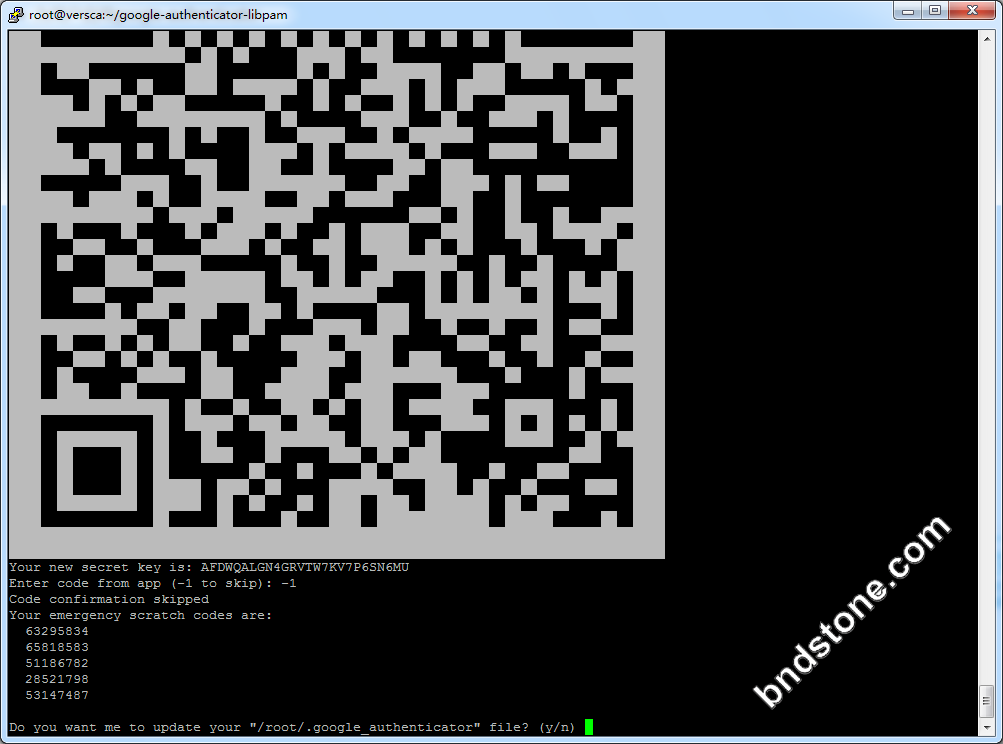
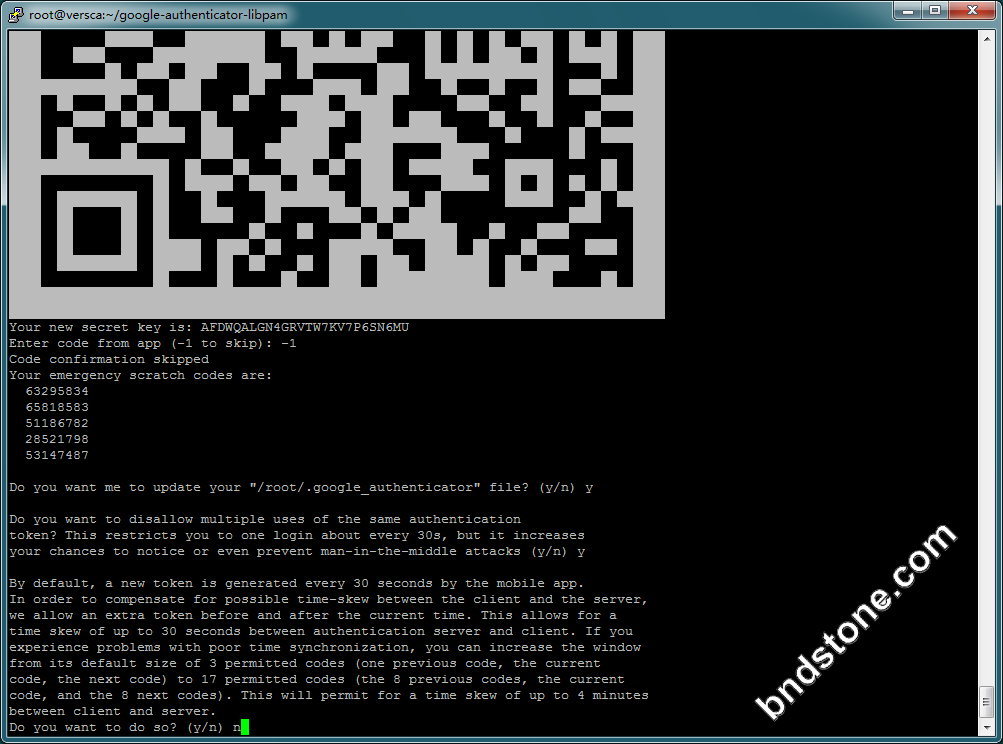
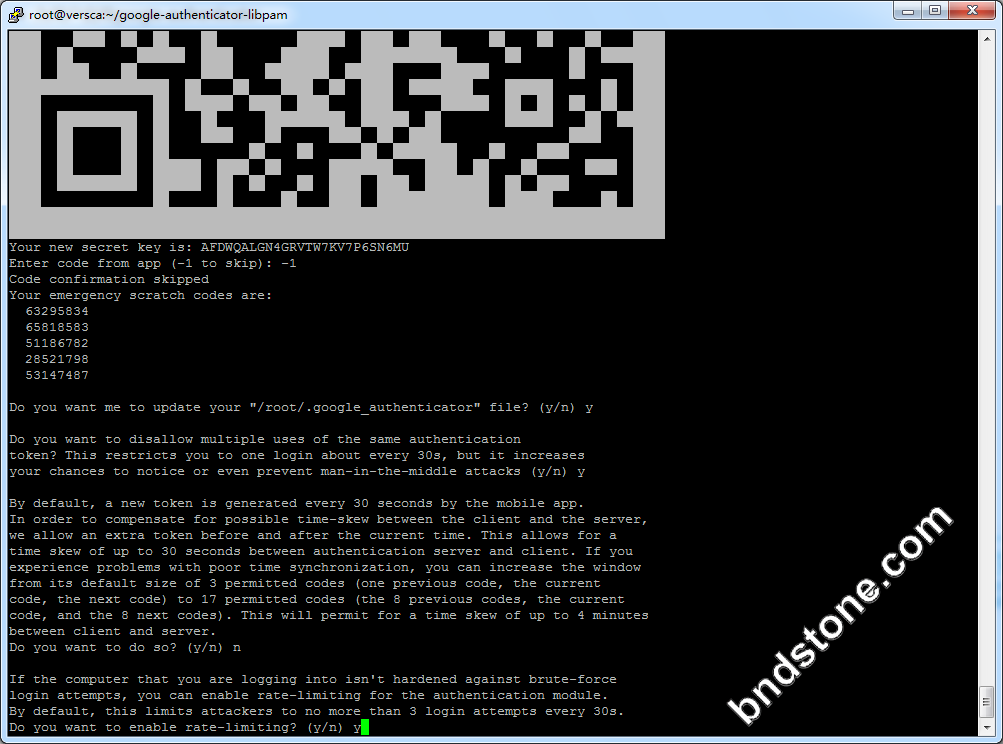
1 2 3 4 5 6 7 8 9 10 11 12 13 | 1) 屏幕提示Do you want authentication tokens to be time-based (y/n) -y 2) 屏幕提示二维码,拿出手机打开google authenticator软件,点击+后选择“条形码扫描"添加认证条目。 注意:将屏幕显示的secret key, verification code 和 recovery codes 保存在安全的地方,供密码恢复使用。 3) Do you want me to update your "/home/sammy/.google_authenticator" file - -[是否更新文件]-y 4) Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) -[是否允许同一认证令牌用于多种用途]- y 4) By default, tokens are good for 30 seconds. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. If you experience problems with poor time synchronization, you can increase the window from its default size of +-1min (window size of 3) to about +-4min (window size of 17 acceptable tokens). Do you want to do so? (y/n) n -[基于时间登录,每个令牌默认的有效时间是30秒,足够抵消客户端到服务器之间的时间延迟] - n 5) If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting (y/n) - [单位时间内显示登录尝试的次数,以防暴力破解,默认每30秒内不能超过3次]- y |
9.关闭google-authenticator验证
修改/etc/pam.d/sshd
1 | vi /etc/pam.d/sshd |
1 | auth required pam_google_authenticator.so nullok #注释掉 |
修改/etc/ssh/sshd_config
1 | vi /etc/ssh/sshd_config |
1 | ChallengeResponseAuthentication yes #注释掉 |
重启sshd
1 | systemctl restart sshd.service |
10. 如果是google cloud vps, 会因为时区不一致而出错,手机上需要跟据服务器时区作出调整.
10-1. 查看当前系统时区
1 | timedatectl | grep "Time zone" #查看当前系统时区 |
显示
1 | Time zone: UTC (UTC, +0000) |
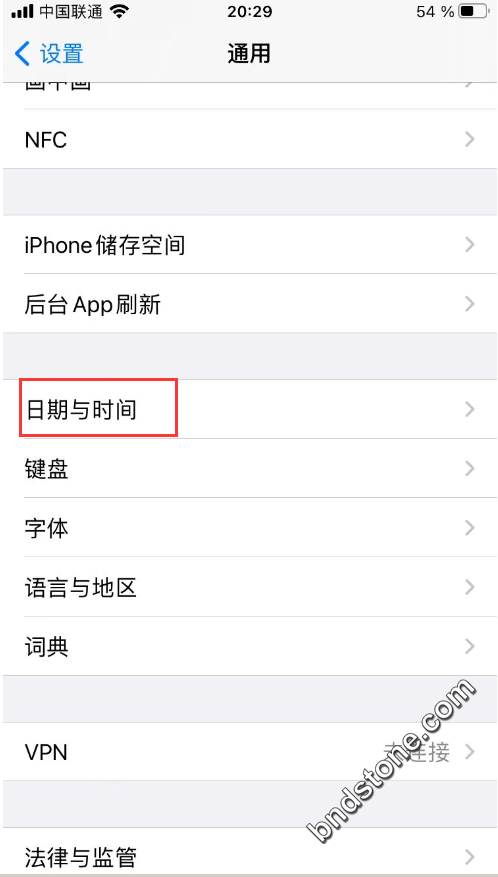
10-2. 说明手机时区要改成 雷克雅未克时间 [冰岛] ,否则Google Authenticator 显示不准
10-3. 修改国家
【设置】-【通用】-【语言与地区】-【地区: 冰岛】


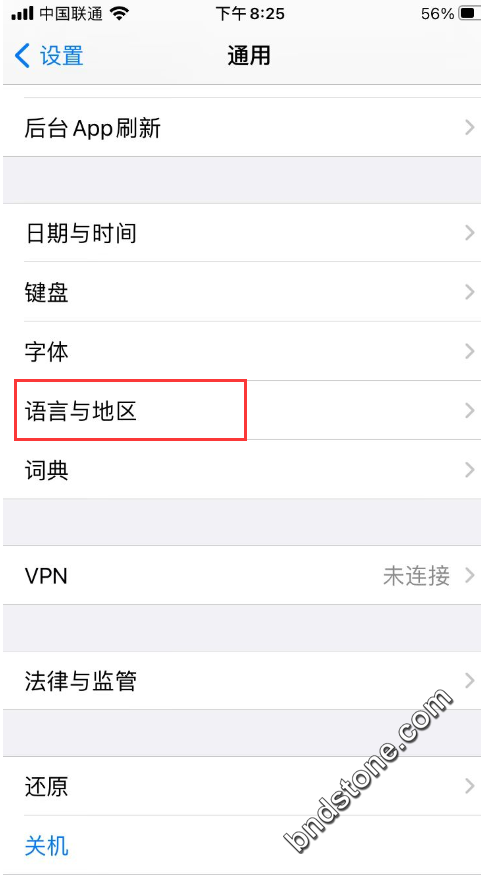

10-4. 关闭定位
【设置】-【隐私】-【定位:关闭】

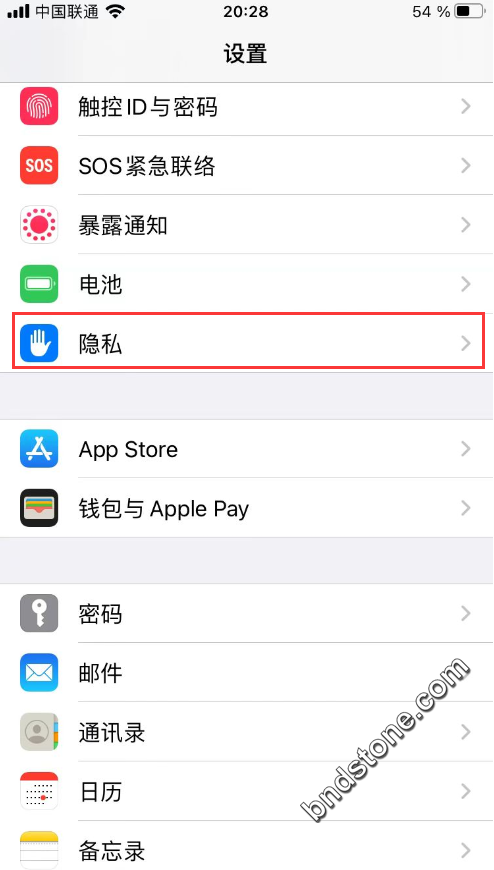
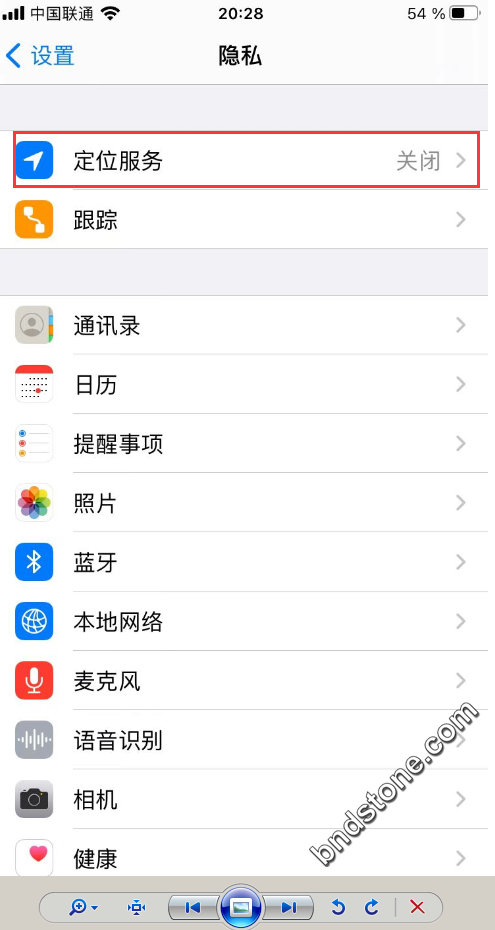
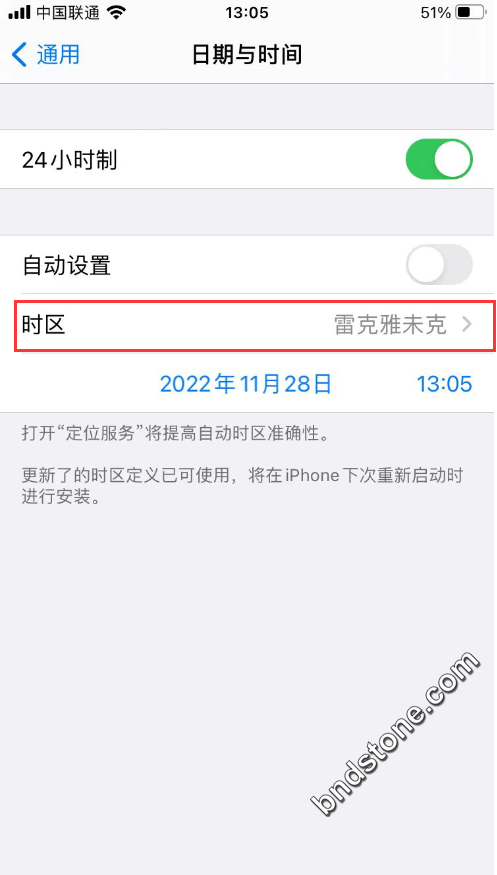
10-5. 修改时区
【设置】-【通用】-【日期与时间】-【时区:雷克雅未克】