CentOS 系统上,让Nginx 配置 Let’s Encrypt 的SSL证书
1 | https://www.linode.com/docs/guides/enabling-https-using-certbot-with-nginx-on-centos-7/ |
1-1. 安装 EPEL
1 2 | yum install -y epel-release yum upgrade -y |
1-2. 安装 snapd
1 | yum install -y snapd |
1-3. 开机自启动 snapd.socket
1 2 | systemctl enable --now snapd.socket systemctl start snapd.socket |
1-4. 建立软链接
1 | ln -s /var/lib/snapd/snap /snap |
2-1. 安装 Certbot
1 | snap install --classic certbot |
会出现如下报错
1 | error: too early for operation, device not yet seeded or device model not acknowledged |
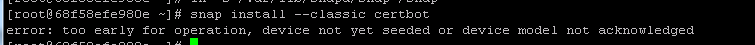
原因: 因为 selinux 导致 snapd.socket 没有成功开启,
2-2. 寻找解决办法:
2-2-1. 查看 snapd.socket ,果然没开启
1 | systemctl status snapd |
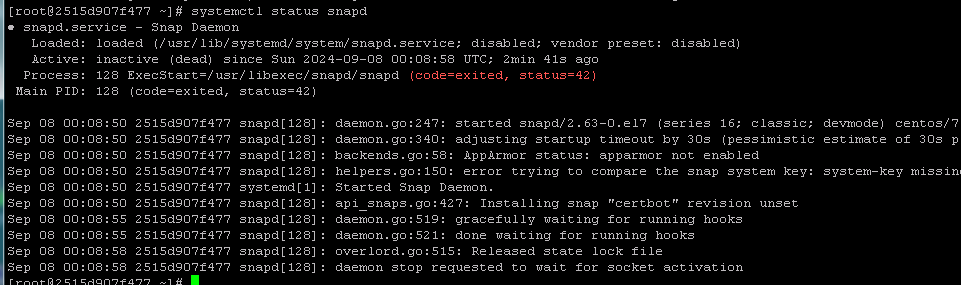
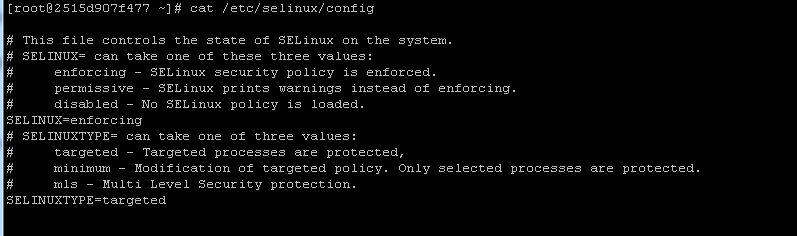
2-2-2. 查看 selinux ,果然 enforcing .
1 | cat /etc/selinux/config |
2-2-3. 解决办法:
1 | vi /etc/selinux/config |
1 | SELINUX=disabled |
重启, Selinux才能生效
1 | reboot |
3-1. 重新安装 Certbot
1 | snap install --classic certbot |

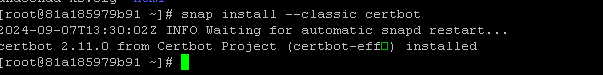
2-3. 建立软链接
1 | ln -s /snap/bin/certbot /usr/bin/certbot |
3-1. 查看是否已经可以运行.
1 | certbot --nginx |
会返回如下信息:
1 2 3 | Saving debug log to /var/log/letsencrypt/letsencrypt.log The nginx plugin is not working; there may be problems with your existing configuration. The error was: NoInstallationError("Could not find a usable 'nginx' binary. Ensure nginx exists, the binary is executable, and your PATH is set correctly.") |
原因: 还没安装nginx.service
4-1. 安装Nginx
1 | https://zls.bndstone.com/4806.html |
1 2 | yum install -y epel-release yum install -y nginx |
4-2. 文件位置
1 2 | /usr/sbin/nginx //启动文件 /etc/nginx/nginx.conf //配置文件 |
4-3. 开启及关闭nginx
1 2 3 4 5 6 | systemctl status nginx.service //查看nginx是否已开启 systemctl start nginx.service //开启nginx systemctl stop nginx.service //关闭nginx systemctl restart nginx.service //重启nginx systemctl enable nginx.service //打开开机自启动nginx systemctl disable nginx.service //关闭开机自启动nginx |
5-1. 开始配置 zls.bndstone.com
1 | cp /etc/nginx/nginx.conf /etc/nginx/nginx-cp.conf //复制一份原始的备用 |
5-2. 修改配置
1 | vi /etc/nginx/nginx.conf |
1 | 修改 server_name 后面改成 zls.bndstone.com |
5-3. 申请证书
1 2 | certbot --nginx -d zls.bndstone.com 271824820@qq.com |
5-4. 会得到证书
1 2 3 4 | Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/zls.bndstone.com/fullchain.pem Key is saved at: /etc/letsencrypt/live/zls.bndstone.com/privkey.pem This certificate expires on 2025-09-12. |
5-5. 配置文件copy放到证书里
1 | mv /etc/nginx/nginx.conf /etc/letsencrypt/live/zls.bndstone.com/zls.bndstone.com.conf |
6-1. 开始配置 bndstone.com
1 | cp /etc/nginx/nginx-cp.conf /etc/nginx/nginx.conf |
6-2. 修改配置
1 | vi /etc/nginx/nginx.conf |
1 | 修改 server_name 后面改成 bndstone.com |
6-3. 申请证书
1 2 | certbot --nginx -d bndstone.com 271824820@qq.com |
6-4. 会得到证书
1 2 3 4 | Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/bndstone.com/fullchain.pem Key is saved at: /etc/letsencrypt/live/bndstone.com/privkey.pem This certificate expires on 2025-09-12. |
6-5. 配置文件copy放到证书里
1 | mv /etc/nginx/nginx.conf /etc/letsencrypt/live/bndstone.com/bndstone.com.conf |
7-1. 开始配置 pic.bndstone.com
1 | cp /etc/nginx/nginx-cp.conf /etc/nginx/nginx.conf |
7-2. 修改配置
1 | vi /etc/nginx/nginx.conf |
1 | 修改 server_name 后面改成 pic.bndstone.com |
7-3. 申请证书
1 2 | certbot --nginx -d pic.bndstone.com 271824820@qq.com |
7-4. 会得到证书
1 2 3 4 | Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/pic.bndstone.com/fullchain.pem Key is saved at: /etc/letsencrypt/live/pic.bndstone.com/privkey.pem This certificate expires on 2025-09-12. |
7-5. 配置文件copy放到证书里
1 | mv /etc/nginx/nginx.conf /etc/letsencrypt/live/pic.bndstone.com/pic.bndstone.com.conf |
…….
…….
…….
依此类推
…….
…….
…….
8. 把 /etc/letsencrypt/live/ 整个文件都传输到 156.238.245.234 .
9. 先申请证书,会失败不要紧
1 2 3 | lnmp vhost add zls.bndstone.com /home/wwwroot/website/zls-bndstone |
10. 把原本成功的 pp.bndstone.com.conf 复制一份,命名 zls.bndstone.com.conf
1 | cp pp.bndstone.com.conf zls.bndstone.com.conf |
11. 修改 zls.bndstone.com.conf
1 | vi zls.bndstone.com.conf |
主要修改 域名, 目录,证书位置
1 2 3 4 5 6 | zls.bndstone.com /home/wwwroot/website/zls-bndstone Certificate is saved at: /etc/letsencrypt/live/zls.bndstone.com/fullchain.pem Key is saved at: /etc/letsencrypt/live/zls.bndstone.com/privkey.pem |
certbot-nginx 安装的是 certbot 1.11.0
1 | https://www.digitalocean.com/community/tutorials/how-to-secure-nginx-with-let-s-encrypt-on-centos-7 |
1-1. 安装 epel-release
1 | yum install -y epel-release |
1-2. 安装 certbot-nginx
1 | yum install -y certbot-nginx |
2-1. 安装 nginx
1 | yum install -y nginx |
1 2 | /usr/sbin/nginx //启动文件 /etc/nginx/nginx.conf //配置文件 |
2-2. 启动nginx.service
1 2 3 4 5 6 | systemctl status nginx.service //查看nginx是否已开启 systemctl start nginx.service //开启nginx systemctl stop nginx.service //关闭nginx systemctl restart nginx.service //重启nginx systemctl enable nginx.service //打开开机自启动nginx systemctl disable nginx.service //关闭开机自启动nginx |
2-3. 修改 nginx.conf
1 | vi /etc/nginx/nginx.conf |
1 | 修改 server_name 后面改成 dns.bndstone.com |
2-4. 验证有没有写错:
1 | nginx -t |
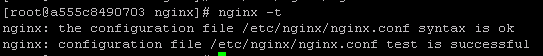
2-5. 验证没错的话,重启nginx.
1 | systemctl reload nginx.service |
3. 更新防火墙
1 2 3 | firewall-cmd --add-service=http firewall-cmd --add-service=https firewall-cmd --runtime-to-permanent |
4. 生成ssl证书
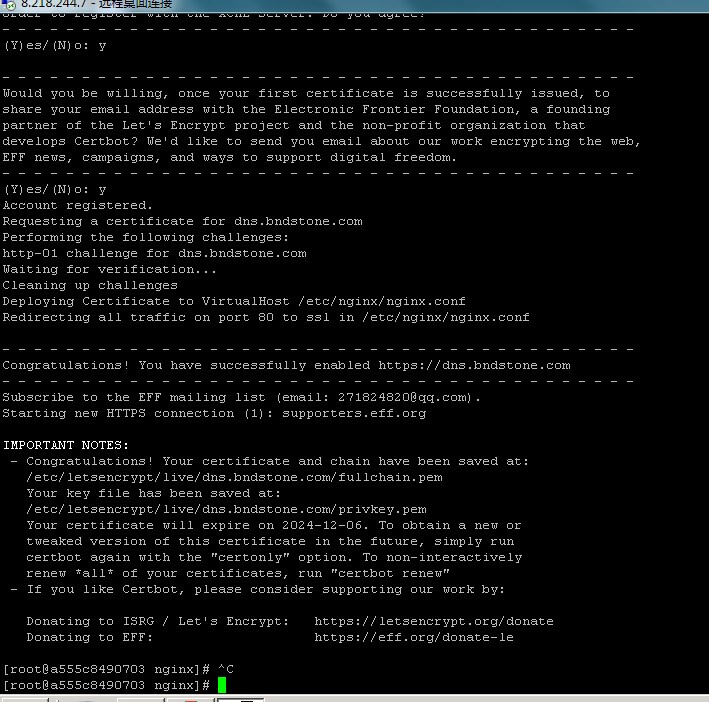
1 | certbot --nginx -d dns.bndstone.com |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 | [root@a555c8490703 nginx]# certbot --nginx -d dns.bndstone.com Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): 271824820@qq.com Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: y Account registered. Requesting a certificate for dns.bndstone.com Performing the following challenges: http-01 challenge for dns.bndstone.com Waiting for verification... Cleaning up challenges Deploying Certificate to VirtualHost /etc/nginx/nginx.conf Redirecting all traffic on port 80 to ssl in /etc/nginx/nginx.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://dns.bndstone.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Subscribe to the EFF mailing list (email: 271824820@qq.com). Starting new HTTPS connection (1): supporters.eff.org IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/dns.bndstone.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/dns.bndstone.com/privkey.pem Your certificate will expire on 2024-12-06. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le |
1 2 3 4 5 6 7 | [root@a555c8490703 nginx]# find / -name '*dns.bndstone.com*' /etc/letsencrypt/renewal/dns.bndstone.com.conf /etc/letsencrypt/live/dns.bndstone.com //证书位置 /etc/letsencrypt/archive/dns.bndstone.com //证书位置 certificate: /etc/letsencrypt/live/dns.bndstone.com/fullchain.pem key: /etc/letsencrypt/live/dns.bndstone.com/privkey.pem |
5. 更新证书,通过crontabs
1 | yum install -y crontabs //安装 crontabs |
1 2 3 4 5 | systemctl status crond.service systemctl start crond.service systemctl stop crond.service systemctl enable crond.service systemctl disable crond.service |
1 | vi /etc/crontab |
6. 更新证书
1 | certbot --nginx certonly -d dns.bndstone.com |
也可以用renew更新所有快到期的证书
1 | certbot --nginx renew |
7. 更多代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 | certbot --help - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - certbot [SUBCOMMAND] [options] [-d DOMAIN] [-d DOMAIN] ... Certbot can obtain and install HTTPS/TLS/SSL certificates. By default, it will attempt to use a webserver both for obtaining and installing the certificate. The most common SUBCOMMANDS and flags are: obtain, install, and renew certificates: (default) run Obtain & install a certificate in your current webserver certonly Obtain or renew a certificate, but do not install it renew Renew all previously obtained certificates that are near expiry enhance Add security enhancements to your existing configuration -d DOMAINS Comma-separated list of domains to obtain a certificate for (the certbot apache plugin is not installed) --standalone Run a standalone webserver for authentication --nginx Use the Nginx plugin for authentication & installation --webroot Place files in a server's webroot folder for authentication --manual Obtain certificates interactively, or using shell script hooks -n Run non-interactively --test-cert Obtain a test certificate from a staging server --dry-run Test "renew" or "certonly" without saving any certificates to disk manage certificates: certificates Display information about certificates you have from Certbot revoke Revoke a certificate (supply --cert-name or --cert-path) delete Delete a certificate (supply --cert-name) manage your account: register Create an ACME account unregister Deactivate an ACME account update_account Update an ACME account --agree-tos Agree to the ACME server's Subscriber Agreement -m EMAIL Email address for important account notifications More detailed help: -h, --help [TOPIC] print this message, or detailed help on a topic; the available TOPICS are: all, automation, commands, paths, security, testing, or any of the subcommands or plugins (certonly, renew, install, register, nginx, apache, standalone, webroot, etc.) -h all print a detailed help page including all topics --version print the version number |